Cloud programmes do not fail for lack of ambition, they stall because value arrives too slowly. Budgets get consumed by groundwork, security sign off happens late, and teams struggle to ship anything meaningful into production. The fix is not more tools, it is an execution playbook that packages proven patterns so your first production value lands fast, with safety and cost control built in.
This article outlines the enterprise cloud solutions and operating patterns that consistently compress time to value for large organisations. It combines field lessons from platform engineering, DevOps and FinOps work, and it shows where Tasrie IT Services helps clients turn months into weeks without compromising security or reliability.

What time to value really means in the enterprise
There are two milestones that matter:
- Time to first value, the time from project start to the first production release that real users benefit from.
- Time to full value, the time to reach scale, resilience, compliance and unit economics that hold up under audit and growth.
To keep both honest, track a small set of metrics. The DevOps Research and Assessment community has shown that teams who optimise lead time, deployment frequency, change failure rate and time to restore deploy faster and more safely. See the research at dora.dev.
Recommended metrics to baseline and trend:
- Lead time for changes, commit to production
- Deployment frequency, per service
- Change failure rate, percentage of releases that require remediation
- Mean time to recovery, from alert to restore
- Environment provisioning time, dev to prod
- Cost per customer transaction, or per service per month
The blockers that slow time to value
Most delays come from a predictable set of anti patterns:
- Starting from a blank page, landing zones, identity, networks and guardrails assembled ad hoc slow everything later.
- Security bolted on late, creates rework and sign off delays.
- Reinvented pipelines for every team, no paved road means toil and drift.
- Big bang migrations, trying to move the whole estate before proving the model.
- No early observability or cost visibility, teams fly blind and cannot prove progress or savings.
Five accelerators that reliably speed time to value
1) Landing zone as code, day one
Codified landing zones establish accounts or subscriptions, identity, baseline networks, encryption, logging, and policy guardrails from the start. Whether on AWS, Azure or GCP, build this with Infrastructure as Code and policy as code so controls are repeatable and auditable, and so platform changes are versioned.
Results inside 30 days:
- Secure-by-default environments ready for app teams
- Consistent networking and identity patterns
- Automated evidence for audit and compliance reviews
Typical pitfalls avoided: snowflake environments, manual tickets for access, late security sign off.
2) Golden paths and an internal developer platform
Golden paths are opinionated templates that create a new service, pipeline and runtime with one command. An internal developer platform then provides self service for environments, secrets, and deploys. The right level of opinionation reduces cognitive load and speeds onboarding.
Results inside 30 days:
- One template to create a production ready microservice with CI, tests and deployment strategy prewired
- Standardised telemetry, so every service logs, emits metrics and traces consistently
- Preview environments on pull request, faster feedback
Typical pitfalls avoided: hand crafted pipelines, inconsistent security controls, drift.
3) Thin slice migration, not big bang
Pick one critical user journey or one bounded context, then apply a strangler pattern to move it first. This creates a real production reference that proves your architecture, security and operations approach without risking the whole portfolio.
Results inside 30 days:
- A live production slice carrying real traffic
- A blueprint for the next two to three slices
Typical pitfalls avoided: portfolio paralysis, hidden integration risk discovered too late.
4) CI/CD with security as a built in quality gate
Automate builds, tests and deployments for every service, and integrate security scanning and policy checks as standard. Adopt GitOps for Kubernetes so the desired state is declared in Git, changes are pull based, rollback is fast and audit trails are automatic.
Results inside 30 days:
- One trunk based CI pipeline template, reused across services
- Automated unit, integration and smoke tests, plus SAST and dependency scanning
- Pull based deployments with progressive delivery options
Typical pitfalls avoided: manual releases, inconsistent checks, slow and risky rollbacks.
5) Observability and FinOps from day one
Instrument services for metrics, logs and traces at the template level, then stand up a cost and utilisation view by team and service. This lets you prove performance improvements and cost reductions alongside feature delivery.
Results inside 30 days:
- Service health dashboards tied to user journeys and SLOs
- Cost by namespace or service, early rightsizing opportunities
Typical pitfalls avoided: unbounded telemetry costs, inability to justify the programme, late performance surprises.
Summary of accelerators and the value they unlock
| Accelerator | 30 day outcome | Effort | Anti pattern avoided |
|---|---|---|---|
| Landing zone as code | Secure, audited environments ready for apps | Medium | Snowflake infra and late security reviews |
| Golden paths and IDP | One command to create a production ready service and pipeline | Medium | Hand built pipelines, inconsistent standards |
| Thin slice migration | First production slice proving architecture and ops | Low | Big bang programme risk |
| CI/CD with security gates | Repeatable delivery with built in checks and fast rollback | Medium | Manual releases, uneven quality |
| Observability and FinOps | SLO dashboards and cost by service visibility | Low | Flying blind on performance and spend |
Effort is indicative, it varies by estate size, compliance scope and in house skills.
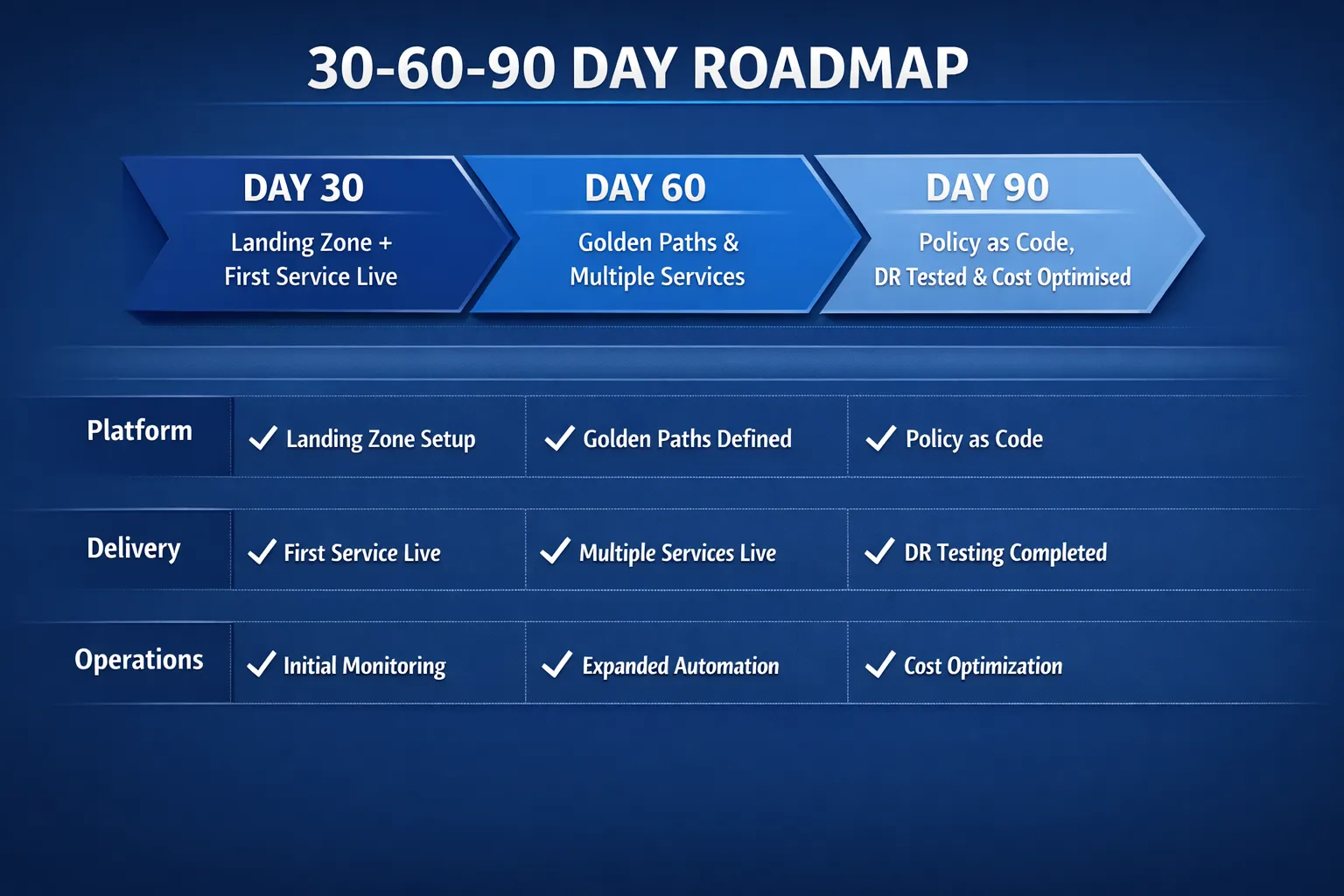
A practical 30, 60, 90 day fast track
Day 0 to 30, foundation and first value
- Baseline metrics, value streams, platform and cost
- Stand up landing zone as code and core identity and network patterns
- Ship golden path v1 for one or two service types, web API and batch are common
- Bootstrap CI pipelines with tests, scanning and GitOps delivery
- Instrument the first service and publish SLOs and cost views
Deliverable, first production slice live behind a feature flag or on a subset of traffic.
Day 31 to 60, scale the paved road
- Expand the internal developer platform with self service environment creation
- Add progressive delivery patterns, blue green or canary
- Extend observability, synthetic checks and burn rate alerts tied to SLOs
- Start a second and third thin slice, reuse the templates
Deliverable, three to five services on the platform, measurable lead time and MTTR improvements.
Day 61 to 90, production hardening and optimisation
- Backup and recovery, disaster recovery pattern chosen and tested
- Policy as code for preventive and detective controls, drift detection in place
- Cost optimisation quick wins applied, rightsizing and autoscaling
- Runbooks written, on call and incident response exercised
Deliverable, platform ready for broader migration waves, governance by code and a clear cost baseline to track savings.
Governance that protects speed, policy as code
The fastest teams do not skip controls, they codify them. Apply guardrails in code so teams move quickly inside safe boundaries. For reference patterns and design principles, the AWS Well Architected Framework is a useful lens across operational excellence, security, reliability, performance and cost.
Key practices:
- Preventive controls, service control policies and least privilege roles
- Detective controls, drift detection and automatic evidence capture
- Release policies, required checks on pull requests and environment promotions
Proof points from the field
- Migrating to Kubernetes with a consultant led approach, a mid market SaaS firm achieved zero downtime cutover, 95 percent faster deployments and significant cost reduction. See the full story, How a Mid Market SaaS Company Saved $253K on Kubernetes Migration.
- You do not need expensive boxes to be secure or fast. During a monitoring uplift, replacing an enterprise API gateway with a Kubernetes native solution saved roughly 100,000 USD over three years with no downtime, read, USD 100K Saved by Replacing Enterprise API Gateway During Prometheus Setup.
- FinOps starts with visibility, then architecture choices. A 70 percent spot, 30 percent on demand mix with safe disruption policies drove a 30 percent EKS bill reduction, see, 30% Cost Reduction in AWS EKS Monthly Bill Through Spot Instance Optimization.
If you are exploring cost levers specifically for Kubernetes, this practical playbook helps, Kubernetes FinOps, Cut Cluster Costs Fast.
What other industries teach us about time to value
Outside technology, clear journeys reduce friction and speed outcomes. In housing, a simple three step buying guide that sets budget, location and inspection expectations helps buyers progress confidently and move in sooner. Your platform should do the same for engineers, a crisp path from idea to production with expectations, controls and support made obvious.
Decision checklist for CTOs and platform leaders
- Can a new team deploy a templated service to production in under a week, without tickets
- Do golden paths enforce security, testing, observability and cost tags by default
- Are SLOs and burn rate alerts defined for the top three user journeys
- Can you show cost by team and service, and are rightsizing opportunities tracked
- Is there a tested recovery plan and a documented rollback for each deployment strategy
- Are policies versioned in Git and enforced automatically, not via manual gates
If the answer is no to two or more, your time to value will suffer.
How Tasrie IT Services helps you win the first 90 days
We focus on measurable outcomes, not tool proliferation. Typical engagements pair your engineers with senior consultants who build side by side, so capability remains after we leave. Workstreams usually include landing zones and guardrails, golden paths and CI/CD, GitOps for Kubernetes where relevant, observability and FinOps, security integration and a thin slice migration that proves the model in production.
You get production grade foundations and the operating practices to sustain them, with value visible to executives and engineers within the first month.
Ready to compress your time to value, contact Tasrie IT Services to discuss a 30, 60, 90 day plan tailored to your portfolio.