Moving from a monolith to microservices is often described as a purely technical migration. In practice, it is a product strategy and an operating model change, and the engineering work only succeeds when those three stay aligned. Done well, cloud native development helps teams ship more frequently, recover faster, and scale without turning every change into a high-risk release.
This guide explains what “cloud native” really means, why (and when) microservices make sense, and how to modernise safely without a big-bang rewrite.
What cloud native development actually means (beyond containers)
“Cloud native” is frequently reduced to “we use Kubernetes”, but the idea is broader. The Cloud Native Computing Foundation (CNCF) describes cloud native as technologies and practices that enable scalable, resilient systems in dynamic environments (public, private, and hybrid cloud).
In practical terms, cloud native development usually implies:
- Applications are designed for automation (deployment, scaling, recovery)
- Infrastructure is defined and managed as code
- Delivery is continuous, with safe rollouts and fast rollbacks
- Observability is built-in (metrics, logs, traces, and meaningful alerting)
- Security and compliance are engineered into the pipeline (DevSecOps)
Microservices can support these goals, but they are not the definition.
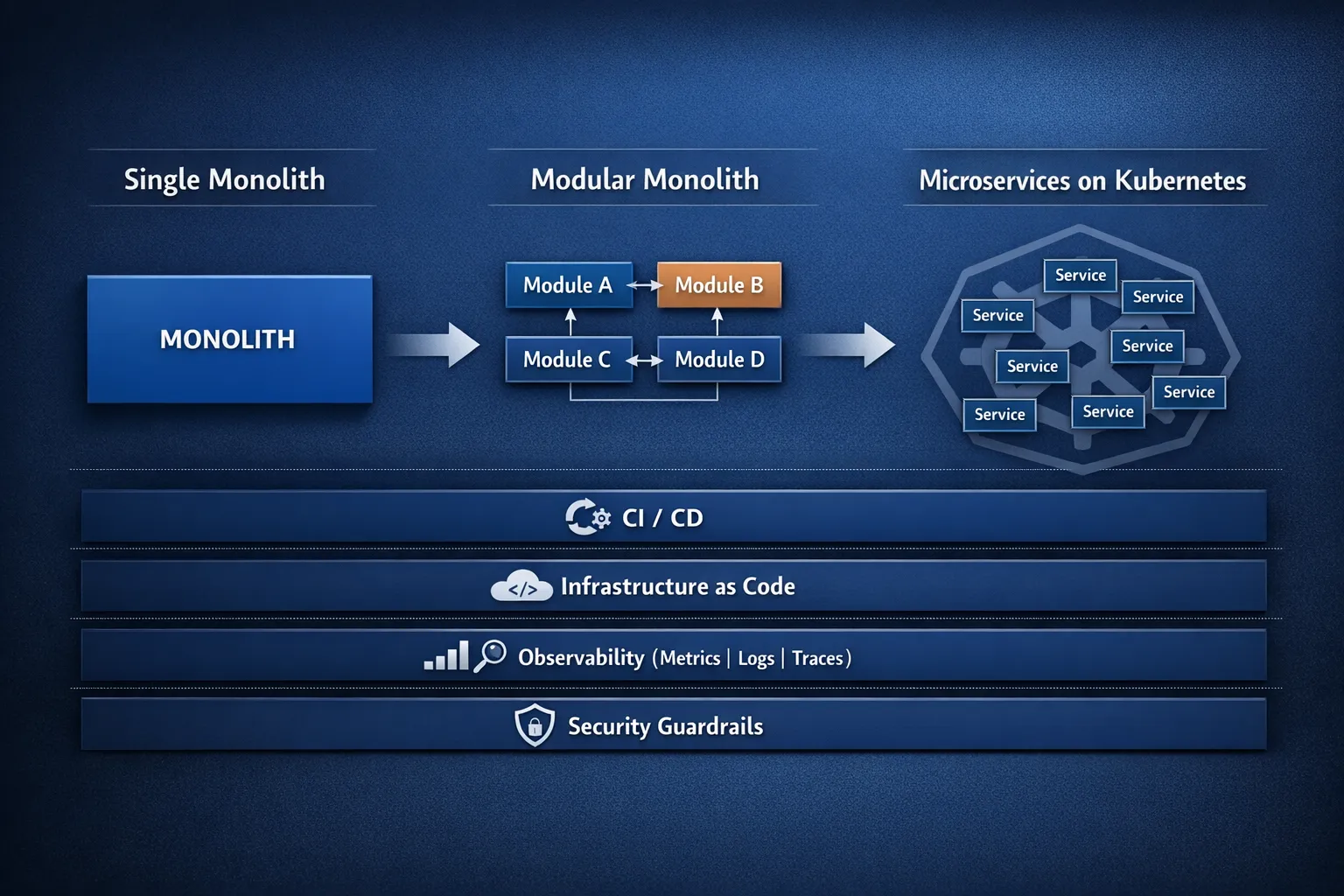
Monoliths, modular monoliths, and microservices: the trade-offs
Many teams jump from “monolith” straight to “microservices”, skipping a crucial middle ground: the modular monolith. A modular monolith can deliver a large percentage of the benefits (clear boundaries, independent ownership, safer refactors) without the operational overhead of distributed systems.
| Architecture style | What it is | Strengths | Watch-outs | Best fit |
|---|---|---|---|---|
| Monolith | One deployable unit, often tightly coupled | Simple deployment, easy debugging, low ops overhead | Release risk grows over time, scaling can be coarse, team coordination becomes a bottleneck | Early-stage products, small teams, low change volume |
| Modular monolith | One deployable unit with strict module boundaries | Strong domain boundaries, faster refactors, often the best “first modernisation” step | Requires discipline (enforced boundaries), still a single deployment | Mid-stage systems, teams preparing for selective service extraction |
| Microservices | Multiple independently deployed services | Independent scaling and delivery, resilience by isolation, team autonomy | Distributed complexity (latency, data consistency, testing, incident response) | Clear domains, high change volume, multiple teams, strong platform maturity |
A useful mental model: microservices buy organisational scale, but you pay in platform and operational complexity.
Why teams break a monolith (and what they really want)
Engineering leaders rarely want microservices for their own sake. They want outcomes such as:
- Shorter lead time from commit to production
- Higher deployment frequency with lower change failure rate
- Faster incident recovery and less “all-hands” firefighting
These are the kinds of capabilities tracked in the DORA metrics, and they are strongly correlated with delivery performance when measured consistently.
Microservices can help, but only if the platform and practices keep pace.
A safer modernisation approach: evolve, do not rewrite
Big rewrites fail because they turn your product roadmap into a multi-quarter “migration project” with uncertain delivery. Cloud native programmes are more reliable when they adopt incremental patterns.
Common decomposition patterns that reduce risk
Strangler pattern You route a small set of functionality to a new service while the monolith continues to serve the rest. Over time, more routes move to the new services. This keeps releases small and reversible.
Extract by domain, not by layer Avoid “auth service”, “database service”, or “utilities service” as your first cuts. Prefer bounded contexts (for example billing, orders, notifications) informed by Domain-Driven Design.
Start with the edges Services like notifications, reporting, file processing, search indexing, and asynchronous integrations are often lower risk to extract first because they naturally decouple.
Prefer asynchronous integration when appropriate Events and queues can reduce tight coupling and protect the core system from downstream slowness, but they also demand stronger observability and data modelling discipline.
If you want a deeper primer on cloud native patterns and common pitfalls, see Tasrie IT Services’ guide on Cloud Native Fundamentals: Patterns, Pitfalls, Payoffs.
The platform you need before microservices feel “easy”
Microservices increase the number of moving parts. Cloud native development works when you invest in the engineering platform that makes change routine.
Key capabilities that reduce microservices friction
CI/CD with safe release strategies Automate build, test, and deployment, then add progressive delivery patterns (blue-green, canary) so teams can release frequently without betting the business on every change.
Infrastructure as Code (IaC) Provision environments repeatably and reduce configuration drift. IaC also improves auditability and makes recovery and scaling less manual.
Observability by default In a monolith, “check the logs” might work. In microservices, you need correlation. OpenTelemetry, structured logging, and service-level dashboards turn debugging from guesswork into investigation.
Security as an engineering workflow Shift security left with image scanning, dependency management, secrets handling, least privilege IAM, and policy-as-code. This is especially important when the number of deployables multiplies.
Reliable service-to-service communication Standardise timeouts, retries, backoff, and circuit breakers. Without these, microservices become a distributed failure amplifier.
Data is where most migrations get stuck
The hardest part of breaking up a monolith is rarely the compute layer. It is data ownership.
In microservices, a strong default is each service owns its data, which avoids tight coupling at the database level. However, that introduces hard topics: eventual consistency, data duplication, and cross-service queries.
A pragmatic approach is:
- Define clear system-of-record ownership per domain
- Use events for downstream projections (read models) where needed
- Keep synchronous calls for “must be consistent now” flows, but design them explicitly
If teams ignore data boundaries, they often rebuild the same coupling they were trying to escape (just over HTTP instead of in-process calls).
Organisational design: microservices require ownership and standards
Microservices can unblock teams, but only when ownership is real.
That typically means:
- Each service has a clear owner (team or accountable group)
- Service contracts are versioned and documented
- You standardise “golden paths” (templates for logging, metrics, CI/CD, security, deployment)
This is where platform engineering becomes a force multiplier. A small platform team can enable many product teams, but only if they treat the platform as a product with adoption, usability, and feedback loops.
There is a useful parallel here: engineering outcomes improve when systems are automated and measured end-to-end. The same mindset applies outside engineering too. If your cloud native programme is part of a broader push for operational automation and measurable performance, a specialist partner in premium AI automation and performance marketing can be relevant for teams modernising go-to-market systems alongside their product platform.
Common microservices pitfalls (and how to avoid them)
Teams do not usually fail because Kubernetes is “too hard”. They fail because the architecture and operations were not designed for distributed reality.
- Distributed monolith: Services exist, but everything depends on everything. Fix by enforcing domain boundaries, reducing synchronous fan-out, and improving contracts.
- Chatty interfaces: Too many calls per user request increases latency and failure probability. Fix by introducing coarse-grained APIs, caching, or async workflows.
- Inconsistent observability: Some services emit metrics, others do not. Fix by standardising instrumentation and dashboards as part of the “definition of done”.
- Testing gaps: Unit tests pass, but integration fails in production. Fix with contract testing and realistic staging environments.
- Cost surprises: More services can mean more idle capacity and higher telemetry volume. Fix with right-sizing, autoscaling policies, and FinOps guardrails.
A pragmatic roadmap: from monolith to cloud native microservices
The most reliable programmes phase the change and prove value early.
| Phase | Focus | Typical deliverables | What “good” looks like |
|---|---|---|---|
| Foundation | Make delivery and environments repeatable | CI/CD baseline, IaC for environments, observability foundations | Releases are routine and reversible, environments are reproducible |
| Modularisation | Improve boundaries inside the monolith | Clear modules, domain ownership, interface boundaries | Fewer cross-cutting changes, faster refactors, simpler releases |
| Extraction | Pull out the right first services | Strangler routing, first services at the edge, service templates | Independent deployments without constant coordination |
| Scale | Standardise and govern | Golden paths, SLOs, policy-as-code, cost controls | Multiple teams ship safely with consistent reliability and security |
A strong first step is a structured baseline of your delivery system, platform maturity, and operational risks. Tasrie IT Services covers how to run this kind of baseline in their DevOps Strategy & Assessment guide.
When you should keep the monolith
It is worth saying plainly: sometimes the best decision is to keep a monolith.
You may not need microservices if:
- The product is early and requirements change weekly
- A single team owns most development
- Performance and scaling needs can be solved with simpler patterns (caching, read replicas, asynchronous processing)
- Your operational maturity is not ready (on-call, monitoring, incident response, CI/CD)
Cloud native development is about reliability and speed. If microservices slow you down, they are the wrong tool right now.
How Tasrie IT Services can help
If you are considering a move from monoliths to microservices, the highest leverage work is usually not “deploy Kubernetes”. It is designing the adoption path so reliability and delivery speed improve at every step.
Tasrie IT Services supports teams with senior, outcome-focused consulting across DevOps, Kubernetes, CI/CD automation, Infrastructure as Code, observability, and security. For a real example of incremental modernisation, see the success story on dockerising and migrating a legacy order system to cloud.
Frequently Asked Questions
Is cloud native development the same as microservices? No. Microservices are one possible architectural style within a cloud native approach. Cloud native is more about automation, resilience, and operational maturity (CI/CD, IaC, observability, security) than any single topology.
Should we rewrite our monolith into microservices? In most cases, a big rewrite is higher risk than an incremental approach. Teams usually get better outcomes by modularising first and then extracting services gradually using patterns like the strangler approach.
What is the best first microservice to extract? Often an edge capability that naturally decouples, such as notifications, file processing, reporting, or search indexing. The “best” choice depends on domain boundaries, data ownership, and operational readiness.
Do we need Kubernetes to be cloud native? Not necessarily. Many teams become significantly more cloud native through CI/CD, IaC, and observability improvements first. Kubernetes can be valuable when you need standardised orchestration and multi-service operations, but it should not be the first milestone by default.
What are the biggest risks when moving to microservices? Data ownership and distributed operations. Without clear domain boundaries, consistent observability, and disciplined service communication patterns, teams end up with a distributed monolith that is harder to run than what they started with.
Ready to modernise without betting the business on a rewrite?
If you are planning a cloud native development programme (or recovering one that has stalled), Tasrie IT Services can help you baseline your current state, design an incremental migration plan, and implement the platform capabilities that make microservices sustainable.
Explore more at Tasrie IT Services and start a conversation about your architecture, delivery, and reliability goals.